

Use Microsoft Granular Delegated Admin Privileges GDAP for Stronger Enterprise Security and Compliance.
- Use Microsoft Granular Delegated Admin Privileges GDAP for Stronger Enterprise Security and Compliance
- What is Microsoft GDAP?
- Strengthen Security – Move from DAP to GDAP in 2022
- GDAP Key to Least Privilege Enforcement
- Microsoft Zero Trust Principles
- Use GDAP for Easier, Faster Compliance
- GDAP for Enterprise Providers – MSP, CSP, Partner
Use Microsoft Granular Delegated Admin Privileges GDAP for Stronger Enterprise Security and Compliance
Microsoft’s Granular Delegated Admin Privileges (GDAP) greatly reduces risk for enterprises and CSP/Partners. Compare the new GDAP security standard to legacy DAP and use GDAP to strengthen your enterprise security and compliance.
Initiatives: Microsoft Security/Compliance | Information Security, Cybersecurity, Compliance
Audience: CCO, CISO, CTO, CIO | IT Executives, Security Executives, Compliance Executives

What is Microsoft GDAP?
Microsoft’s Granular Delegated Admin Privileges (GDAP) is designed to greatly reduce risk for Microsoft enterprise clients.
GDAP allows you to control the access level you give to your employees or providers (MSP, CSP, Partner) for your MSFT cloud services.
| Enterprise Microsoft Access Controls |
Legacy DAP |
*New* GDAP |
|---|---|---|
| Level of Access/Roles | Global Admin + Helpdesk Agent | Custom |
| Relationship Timeline | Indefinite | Custom (Max of 2 years) |
| Invitation Link | Same for every customer | Custom for every customer |
| Security Group Assignment | √ | |
| Activity Logs | √ | |
| Access to Security & Compliance Center | √ | |
| Privileged Identity Management (PIM) Support | √ |
Level of Access/Roles: DAP relationships provide you the roles of Global Admin and Helpdesk admin by default without any ability to change. GDAP will allow you to select more granular level permissions and make that unique per customer. This is extremely important if you work with a provider today and do not want that 3rd party risk.
Relationship Timeline: DAP relationships last indefinitely. The customer accepts the delegated admin link and that relationship is permanent unless you go under Settings>Partner Relationships and remove the relationship. GDAP allows you to create custom timelines for how long the relationship will be in place and there is also a maximum timeframe of 2 years.
Invitation Link: DAP relationship links are universal per region. This means you use the same DAP link for every customer you onboard into Partner Center. GDAP changes that because you will most likely have different levels of access per customer. This means that each invitation will be unique to a specific customer.
Security Group Assignment: There are no layers of assignment when it comes to DAP relationships. The same level of access is given to all members within a Partner Center environment who have access to customers. GDAP allows you to have nested security groups with separate roles, in order to stratify permissions even further. Here is an example of that functionality:
Enterprises can create a Provider tier 1 support group and grant it service support admin and global reader roles, which means the Provider group can create tickets on behalf of the enterprise but cannot make any changes. Enterprises can create a Provider tier 2 support group and grant it high-privilege roles such as Intune admin, Exchange admin, and Dynamics 365 admin.
Activity Logs: With DAP, there are no granular activity logs that show you when delegated access permission are being leveraged from Partner Center and they also do not include any information around the lifecycle of a delegated admin relationship (when it was accepted, when it was removed, etc.). GDAP changes this by providing that visibility in the Azure AD Activity logs on both a Provider level and a customer level.
Access to the S&C Center: This has been a pain point for Providers for years in the fact that DAP does not allow you to enter certain admin portals on behalf of customers through partner centers. The Security and Compliance center (now splitting to two admin centers) has been a good example of this lack of access. GDAP is opening up more flexibly here.
PIM Support: Privilege Identity Management (PIM) is a Microsoft service that allows for “just in time” levels of access. Essentially it allows you to elevate your role for a temporary period of time to perform certain admin tasks. PIM will be coupled with GDAP to allow Providers to elevate privileges into certain security groups that have certain grants/roles into customer environments. This improves security even further.
Strengthen Security – Move from DAP to GDAP in 2022
All Microsoft Cloud services which support DAP will support GDAP and for new Microsoft Cloud workloads only GDAP will be supported.
Once GDAP is in place, enterprises should remove all DAP permissions to secure their tenants. Removing DAP doesn’t remove the Provider relationship, so it doesn’t affect any licensing contracts you may have. This does, however, remove all Provider access via PowerShell and APIs, including Microsoft 365 Lighthouse.
GDAP Key to Least Privilege Enforcement
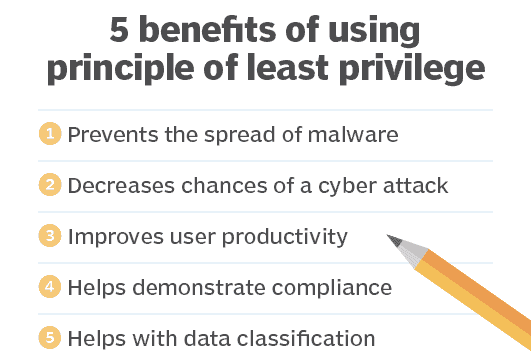
GDAP is the primary mechanism for enterprises to enforce the Principle of Least Privilege (POLP) in their Microsoft cloud environments.
POLP is a concept in computer security that limits users’ access rights to only what are strictly required to do their jobs.
Microsoft GDAP Least Privilege BenefitsUsers are granted permission to read, write or execute only the files or resources necessary to do their jobs. This principle is also known as the access control principle or the principle of minimal privilege.
POLP is one of the three guiding principles of Microsoft’s security strategy known as Zero Trust.
Microsoft Zero Trust Principles
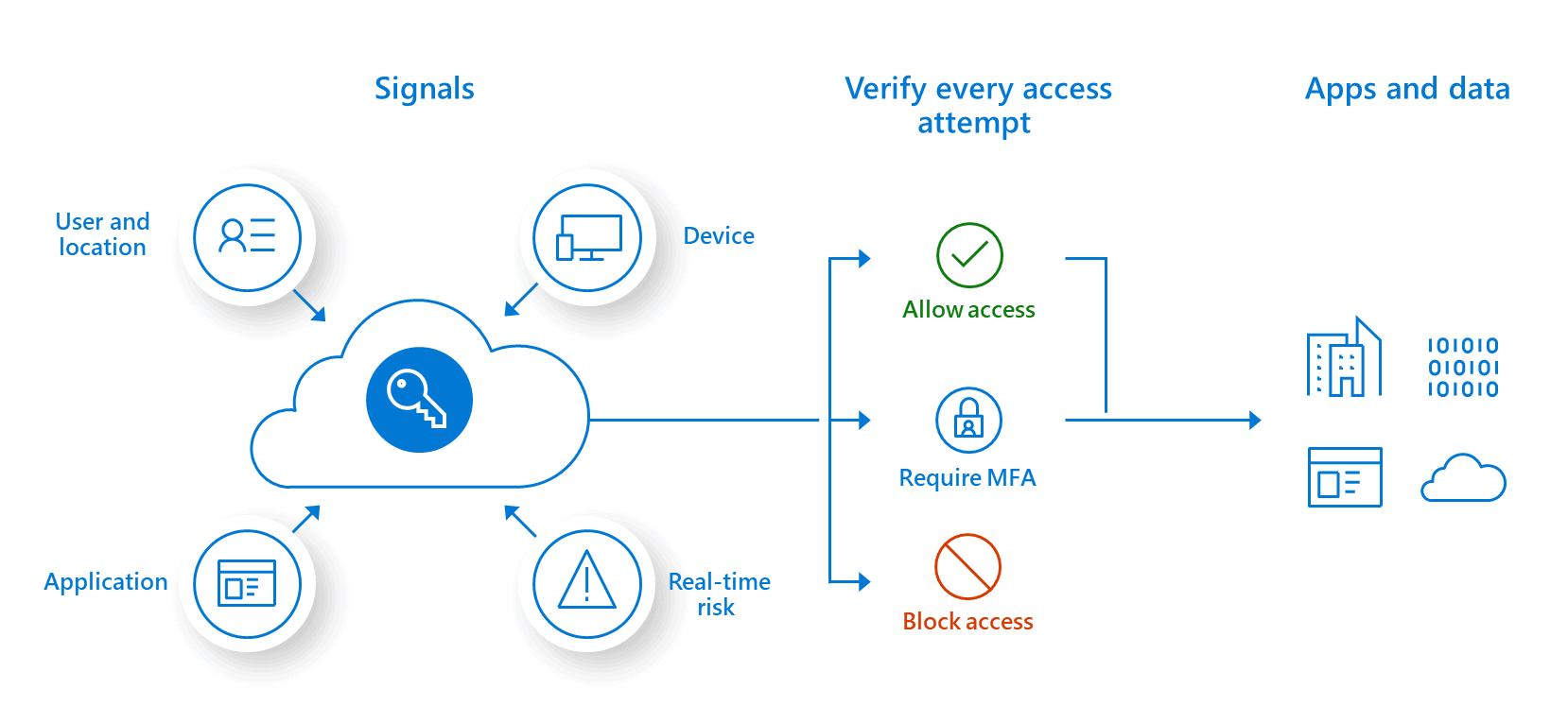
Verify Explicitly – Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
Use Least Privileged Access – Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive polices, and data protection to help secure both data and productivity.
Assume Breach – Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Microsoft Granular Delegated Admin – Zero Trust
Fundamental to Microsoft’s approach for Zero Trust is not to disrupt end users, but work behind the scenes to keep users secure and in their flow as they work.
Use GDAP for Easier, Faster Compliance
GDAP’s least privileged access gives enterprises the policy enforcement tool they need for compliant Microsoft cloud deployments.
GDAP makes it easier to achieve compliance and faster to prove during a compliance audit for:
HIPAA, GDPR, FDDC, FISMA, Government Connect, Federal EO 14028, SOX, ISO, SOC and others.
GDAP least privileged access is strongly recommended by CISA for 2022 and beyond.
Benefits of Least Privilege GDAP
According to the Microsoft Vulnerabilities Report 2021 by BeyondTrust, from the 5 year period of 2016 – 2020, 78% of Critical vulnerabilities on Windows systems could have been mitigated by removing admin rights. In fact, in 2020, 98% of Critical vulnerabilities in Internet Explorer & Edge would have been mitigated by removing admin rights! A similarly powerful risk-reducing power of least-privilege has also been demonstrated across third-party applications, such as for Oracle, Adobe, Google, Cisco, VMware, etc.
Unfettered privileged rights and access essentially equates to uncapped potential for damage. The more privileges a user, account, or process amasses, the greater the potential for abuse, exploit, or error. Implementing least privilege not only reduces the likelihood of a breach occurring in the first place, but it helps limit the scope of a breach should one happen.
Microsoft GDAP least privilege benefits include:
- A condensed Microsoft attack surface: Limiting privileges for people, processes, and applications/machines diminishes the pathways and ingresses for exploit.
- Reduced MSFT malware infection and propagation: Least privilege helps dramatically reduce malware infection and propagation, as the malware (such as SQL injections or ransomware) should be denied the ability to elevate processes that allow it to install or execute.
- Improved operational performance: When it comes to your Microsoft applications and systems, restricting privileges to the minimal range of processes to perform an authorized activity reduces the chance of incompatibility issues cropping up between other applications or systems, and helps reduce the risk of downtime.
- Simpler, audit-friendly compliance: By constraining the possible activities, least privilege enforcement helps create a less complex, and thus, a more audit-friendly, environment. Moreover, many compliance regulations (including HIPAA, PCI DSS, FDDC, Government Connect, FISMA, and SOX) require that organizations apply least-privilege access policies to ensure proper data stewardship and systems security. For instance:
-
- The US federal government’s FDCC mandate states that federal employees must log in to PCs with standard user privileges.
- The HIPAA Privacy Rule provides guidelines for the establishment of least privilege, such as restricting access to data (i.e. a subset of a patient record as opposed to the entire record) base on the “minimum necessary use” to accomplish a specific purpose.
PCI DSS states that organizations that process or store credit card data must restrict access to cardholder data by business need to know, and specifically invokes the use of least privilege user accounts [ 7.1.1 Restriction of access rights to privileged user IDs to least privileges necessary to perform job responsibilities; 7.2.2 Assignment of privileges to individuals based on job classification and function].
GDAP for Enterprise Providers – MSP, CSP, Partner

Granular delegated admin privileges, or GDAP, is available to Providers such as Microsoft CSPs, MSPs, and Partners in early 2022. These changes address supply chain attacks (like Nobelium) and shore up the least privilege pillar of Microsoft’s Zero Trust security model.
Formerly, both distributors (Microsoft Indirect Providers/CSP Tier 1s) and MSPs (Indirect Resellers) had established Delegated Admin Privileges (DAP) with all downstream customers. This allowed distributors to license customer tenants and provide support. It allowed MSPs and Partners the ability to provide support and perform day to day management tasks via Partner Center.
With granular delegated access:
- Providers can control more granular and time-bound access to their customers’ workloads, so that they can address customers’ security concerns.
- CSPs, MSPs, and Partners now have help in addressing concerns about data security which will reduce the likelihood of security incidents and help to make Partners’ and Enterprise ecosystems more secure.
- Providers can restrict access per customer at the workload level of your employees who are managing your customers’ services and environments.
- CSPs, MSPs, and Partners can report on how Provider teams are accessing Enterprise tenants across all tenants.
- Providers can turn off or reduce unused GDAP or DAP connections to help with customer security and mitigate Partner liability.
Enterprise Provider Considerations for GDAP
- Establish a baseline to customer environments: Since Providers now have autonomy to decide what roles they provide in customer tenants, they will have to determine a baseline and/or stratification based on how large their practice is. If an MSP or Partner works with a CSP, you will also need to be asking them what their baseline role is for every customer and request specific roles if applicable. Realistically, MSPs or Partners should be giving CSPs rights to license the tenant and provide a baseline of support.
- Operational Complexities: With GDAP there are now many considerations to work through from an operational standpoint. Outside of deciding levels of access, you also must re-accept GDAP relationships every 2 years (minimum). Additionally, you have custom links per customer environment. Overall, the security benefits outweigh the additional complexity you are going to have to deal with. As a CSP, MSP or Partner, you should be evaluating your levels of access in all tenants periodically for both yourself, customers, and 3rd parties.
- Access to New Admin centers: This is a big win if GDAP allows for delegated access to all of the admin centers (Like S&C center) that Providers have been missing for years. This will prevent Providers from creating Global Admins in Enterprise tenants and sharing MFA across a support team.
- Free Azure AD P2 licensing: Microsoft is giving P2 away for 1 year so Providers can leverage things like PIM. Take advantage of P2 in order to provide more security within your Partner Center environment.
- Remove all DAP permissions: To secure Provider and customer tenants. Removing DAP doesn’t remove the partner relationship, so it doesn’t affect any licensing contracts you may have. This does, however, remove all partner access via PowerShell and APIs, including Microsoft 365 Lighthouse.
